LCMVRAVACONFIG90039 error during vRA 8 deployment
While all prechecks finished succesfully during a vRealize Automation 8 deployment recently vRSLCM threw error LCMVRAVACONFIG90039 while deploying.
To have a better understanding of what went wrong I looked at the vmware_vrlcm.log file on the vRSLCM appliance. This log file contained below error message, indicating something is wrong with the encryption of the certificate.
1-- Error Stream ::
2====================================================
3Invalid encryption or hash algorithm:
4Expected one of: ['SHA224WithRSAEncryption', 'SHA256WithRSAEncryption', 'SHA384WithRSAEncryption', 'SHA512WithRSAEncryption']
5Found: SHA1WithRSAEncryption
6====================================================
This error is generated by vracli while trying to import the certificate on the appliances. Verifying the certificate with vracli gave the same error message.
1vracli certificate ingress --validate ./cert.txt
2
3Invalid encryption or hash algorithm:
4Expected one of: ['SHA224WithRSAEncryption', 'SHA256WithRSAEncryption', 'SHA384WithRSAEncryption', 'SHA512WithRSAEncryption']
5Found: SHA1WithRSAEncryption
Now lets dig a bit deeper in these certificates. The certificate chain consisted of an intermediate and root CA certificate. Deciphering a certificate can done by executing below where cert.txt contains the certificate.
1openssl x509 -in ./cert.txt -text -noout
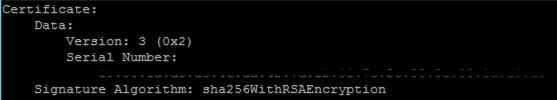
The server certificate uses the supported SHA256WithRSAEncryption signature algorithm.
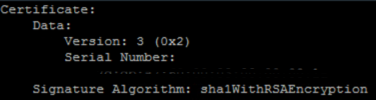
The intermediate CA certificate however was using the unsupported SHA1WithRSAEncryption signature algorithm.
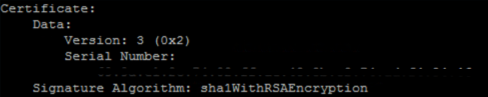
And also the root CA was using the unsupported SHA1WithRSAEncryption signature algorithm.
vRA does not support SHA1 usage in any of the certificates in its certificate chain in versions 8.0 and 8.1. vRA 8.1 patch 1 and vRA 8.2 support SHA1 for the root certificate only.
As SHA1 encryption for certificates has been deprecated since 2017 in modern browsers and most certificate providers stopped issuing SHA1 encrypted certificates by now, you shouldn’t run into this issue that often.
Unfortunately, at he time of publising this post, there is no VMware documentation nor KB article which describes the detailed vRA certificate requirements. Based on the vracli output following SHA2 algorithms are supported on the certificate chain.
- SHA224
- SHA256
- SHA384
- SHA512